Cyber Security Incident Response
Having a well prepared Incident Response (IR) Plan is paramount against today’s threat landscape. A mature and effective IR Plan with access to dedicated IR resources allows you to prioritise threats effectively. Effective containment and eradication will help your Enterprise quickly return to business as usual.
Dealing with cyber security incidents can be frustrating if you don’t have access to the right knowledge and resources.
With so many different types of threats, it’s hard to triage and prioritise them all – particularly if an adversary is bombarding you deliberately.
Sense of Security offers a comprehensive service that dramatically improves Incident Response maturity levels. It includes a dedicated 24 x 7 x 365 Incident Response hotline for peace of mind. Giving you access to the resources and knowledge you need to help execute your IR plan to perfection.
Our Incident Response clients first submit themselves to a thorough assessment, starting with a measure of their baseline Incident Response Readiness.
The Sense of Security consultants then implement and deliver dedicated workshops and materials.
- A Complete Incident Response Plan (IRP)
- Incident Response Policy Documents and IR Management Plans.
- Forms and templates; Breach Notification Forms, Checklists, Incident Identification Forms.
- Easy to understand Incident Response Playbooks & Flowcharts.
- A Communications Policy including dealing with the Media for public breaches.
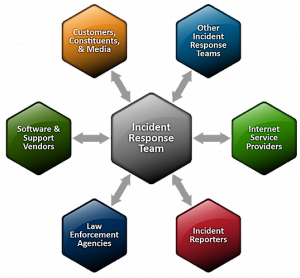
We’ll help you establish and identify your optimal team structure, mapping IR roles and backup personnel to ensure availability at all times.
Good Incident Response relies on good communication – with a plan that is thoughtfully conceived and tested through scenario based exercises.
You can expect comprehensive IR materials written concisely, and specifically for your Enterprise, that contain colour-coded graphic elements making reading a breeze.
Incident Response Playbooks
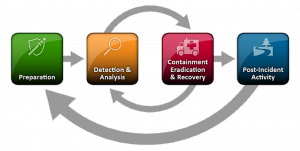
The Sense of Security methodology includes development and delivery of easy-to-understand IR Playbooks. It means your team can make accurate and timely decisions during a crisis.
At each stage of the IR process workflow you’ll understand exactly which IR phase you’re dealing with – Preparation, Detection & Analysis, Containment Eradication & Recovery, or Post-Incident Activity.
Classification of an incident is performed using our unique taxonomy that will have you covered for any type of event:
- Denial of Service or Distributed Denial of Service (DDoS)
- Virus, Malicious Code, Ransomware, Worm or other Malware
- Social Engineering, Phishing, or Insider Threats
- Data Loss or Destruction Incidents
- Active signifcant Port Scanning, or failed Hack attempts
- Third Party risk through Vendors, On or Off-Premise.
Our IR retainer service clients are issued with Playbooks for each of the above, and more.